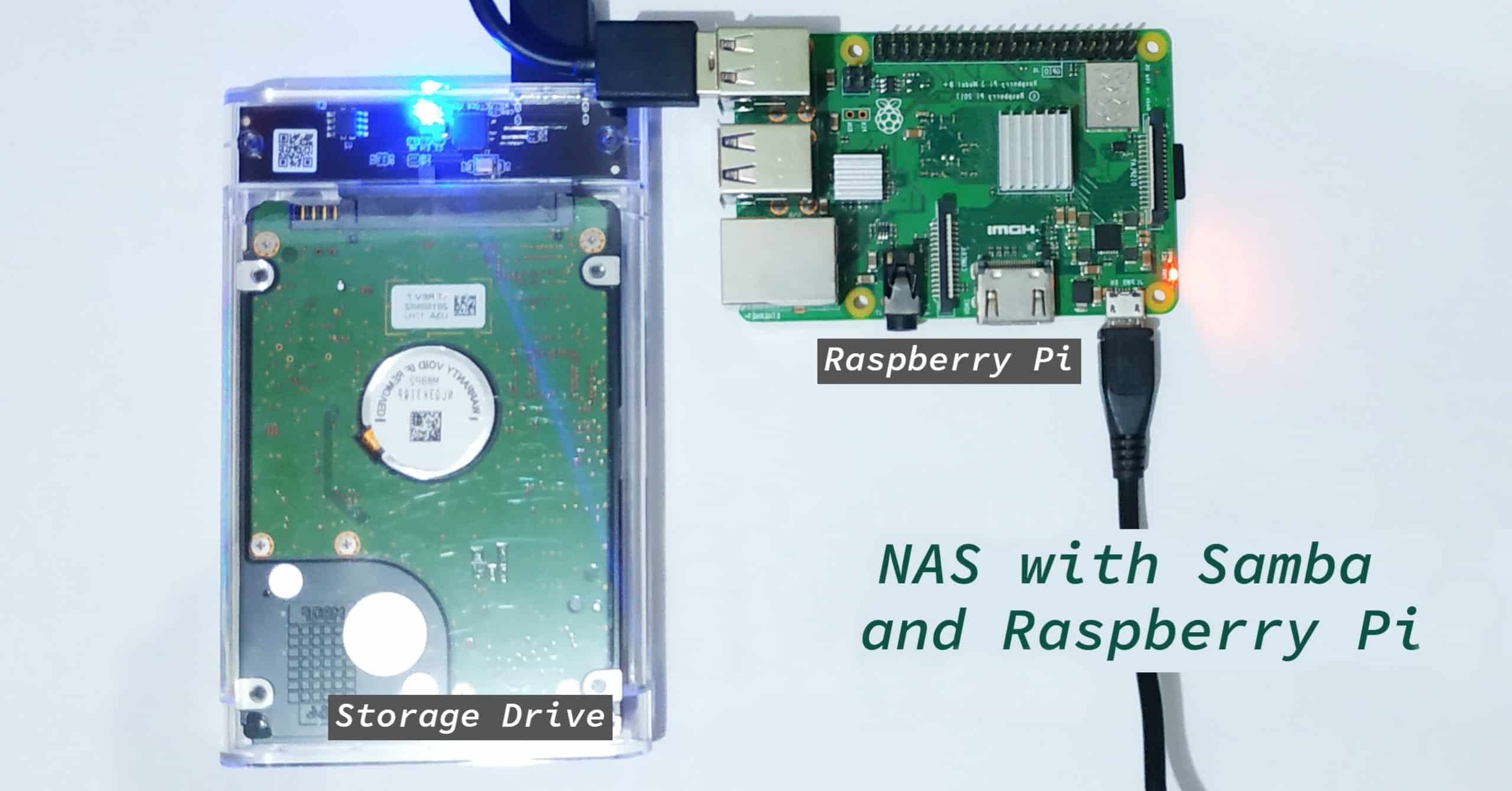
Are you wrestling with the challenge of establishing a secure and dependable connection to your remote IoT devices, specifically those powered by a Raspberry Pi? Securing remote IoT devices using Raspberry Pi is paramount in today's interconnected world, safeguarding your projects and ensuring data integrity.
The advent of the Internet of Things (IoT) has ushered in an era of unprecedented connectivity, with devices ranging from smart home appliances to industrial sensors generating and transmitting data across vast networks. However, this proliferation of connected devices has also created new vulnerabilities, making the secure connection of remote IoT devices an absolute necessity. This comprehensive guide delves into the intricacies of securely connecting remote IoT devices to a Raspberry Pi, particularly focusing on a peer-to-peer (P2P) architecture.
Before we dive into the technical aspects, let's understand the core concepts and importance of securing remote IoT connections. The primary goal is to protect sensitive data, maintain privacy, and prevent unauthorized access to your devices. By implementing secure connections, you can mitigate the risks of cyberattacks, data breaches, and device compromise. This is where the power of secure remote access comes into play, providing a secure and direct pathway to your IoT devices, irrespective of their location.
- Bianca Censori Age More Wiki Career Kanye West Facts
- Ganges River Countries Significance Facts Your Guide
This guide is meticulously crafted to provide a practical approach to achieving this goal. We'll explore the crucial elements, from configuring your Raspberry Pi to setting up a secure Windows environment. Moreover, we'll delve into the realm of free and open-source tools to ensure you can build secure connections without incurring unnecessary costs. The guide will also provide clear instructions on how to establish a secure P2P connection that protects your data and enhances your device's functionality.
Let's consider the landscape of IoT security, and the importance of adopting secure methods for establishing P2P connections. Utilizing a P2P architecture eliminates the reliance on centralized servers, thereby enhancing security and reducing the risk of a single point of failure. This setup enables direct communication between devices, creating a more resilient and secure network.
This article will guide you through the process of connecting a remote IoT device, specifically a Raspberry Pi, in a P2P environment, complete with a free download option for essential software and tools. Whether you're a beginner or an experienced developer, this guide offers comprehensive steps, tips, and tricks to ensure that your setup is efficient and, most importantly, secure.
- Discover Sandalwood A Deep Dive Into Kannada Cinema
- Angel Iris Murphy Brown Mel B Eddie Murphys Daughter Turns 18
Key Advantages of Secure Remote IoT Connections:
- Data Security: Protects sensitive data from unauthorized access and potential breaches.
- Device Control: Provides secure remote access for configuration, monitoring, and control.
- Enhanced Privacy: Reduces the risk of data interception and ensures user privacy.
- Reliability: Improves the stability and resilience of your IoT network.
- Cost-Effectiveness: Optimizes the use of resources and reduces operational expenses.
With remote IoT devices becoming increasingly prevalent, the ability to securely connect them is no longer a luxury, but a necessity. This guide will empower you to establish secure and reliable P2P connections.
Now, let's explore the crucial software and technical skills to ensure that your setup is both efficient and secure. The key elements encompass selecting the right software, installing essential tools, configuring your devices for P2P communication, and adopting the best practices to secure your IoT network.
The security landscape is constantly evolving, thus the need for a continuous learning approach. This guide serves as your starting point, providing the foundational knowledge and practical steps necessary to secure your remote IoT devices. You'll learn how to navigate the complexities of P2P connections, protect your data, and take full control of your devices. Now, let's dive into the core of establishing secure P2P connections.
Core Components of Secure Remote IoT P2P Connections
Securing remote IoT devices in a P2P architecture involves a multi-faceted approach, encompassing both hardware and software considerations. Let's delve into the core components, ensuring that your setup is robust, reliable, and capable of withstanding potential threats.
1. Raspberry Pi Configuration: Your Raspberry Pi will act as the central hub, responsible for initiating and managing secure connections. This involves several steps:
- Operating System Installation: Begin by installing a suitable operating system, such as Raspberry Pi OS (formerly Raspbian), on your Raspberry Pi. Ensure that the OS is up-to-date and secure.
- Network Configuration: Configure your Raspberry Pi to connect to your local network. This typically involves setting up a static IP address to ensure reliable connectivity.
- SSH Access: Secure Shell (SSH) is a secure protocol used for remote access. Enable SSH and ensure that it's properly configured. Consider changing the default SSH port and implementing strong password practices.
2. Software Selection and Installation: Choosing the right software for secure IoT connections is critical. This guide focuses on open-source, free tools to keep costs low.
- WireGuard: WireGuard is a modern, fast, and secure VPN protocol. It is an excellent choice for creating secure P2P connections. Install WireGuard on your Raspberry Pi and configure it to establish a secure VPN tunnel.
- Other Utilities: Consider installing tools like `net-tools` (for network management) and `tcpdump` (for network traffic analysis).
3. P2P Configuration: The P2P setup allows direct communication between devices without relying on a central server. Here's how to configure your devices for P2P connection:
- Generating Keys: Generate cryptographic keys for your Raspberry Pi and your remote IoT devices. These keys are essential for establishing secure communication.
- WireGuard Configuration: Configure WireGuard on both the Raspberry Pi and your remote devices. Specify the public keys, IP addresses, and ports required for communication.
- Firewall Rules: Configure firewall rules on your Raspberry Pi to allow traffic through the WireGuard interface.
4. Windows Environment Configuration: To access your Raspberry Pi from your Windows system, you'll need to configure your environment properly.
- SSH Client: Use an SSH client like PuTTY or OpenSSH to connect to your Raspberry Pi securely.
- File Transfer: Use secure file transfer protocols (SFTP) to transfer files between your Windows system and Raspberry Pi.
- Remote Desktop: If you need a graphical interface, consider using a remote desktop protocol like VNC.
5. Security Best Practices: Securing your IoT network is an ongoing process, necessitating regular updates and vigilant monitoring.
- Regular Updates: Keep your operating systems and software up-to-date to patch any security vulnerabilities.
- Strong Passwords: Use strong, unique passwords for all your devices and accounts.
- Network Segmentation: Isolate your IoT devices from your main network to limit the impact of potential breaches.
- Monitoring and Logging: Implement monitoring and logging to detect suspicious activity and troubleshoot issues.
- Firewall Rules: Regularly review and update your firewall rules to restrict unnecessary network access.
By implementing these components, you create a secure and reliable foundation for your remote IoT connections. Regular assessment and monitoring are critical to maintain the security and functionality of your setup.
Choosing the Right Software
The selection of the right software is a cornerstone of establishing secure remote IoT P2P connections. The market is overflowing with tools, protocols, and solutions. The goal is to choose options that are secure, reliable, and compatible with your Raspberry Pi and other IoT devices. The best approach involves utilizing open-source, free tools to keep costs down.
Here's a breakdown of the key software choices, the rationale behind each selection, and considerations for optimal performance and security:
1. WireGuard: The Modern VPN Protocol
WireGuard is a secure and modern VPN protocol that offers exceptional performance and ease of use. It's designed to be leaner and more efficient than older VPN protocols, such as OpenVPN. WireGuard provides a fast and secure tunnel for your P2P connections. Key advantages include:
- Simplicity: Easy to set up and configure.
- Speed: Provides superior performance due to its efficient codebase.
- Security: Uses strong cryptographic algorithms.
- Open-Source: Freely available and actively maintained.
2. SSH Clients: Secure Remote Access
SSH is the standard protocol for secure remote access to your Raspberry Pi. An SSH client allows you to establish a secure connection, execute commands, and transfer files. Recommendations include:
- PuTTY: A popular, free SSH client for Windows.
- OpenSSH: A built-in SSH client available in many operating systems, including Windows (requires installation).
3. File Transfer Protocols (SFTP/SCP): Secure File Management
SFTP and SCP are secure protocols for transferring files between your Windows system and your Raspberry Pi. They provide encryption, preventing unauthorized access to your data during transit. Both protocols are integral parts of SSH. Consider these tools:
- FileZilla: A free and user-friendly SFTP client.
- WinSCP: Another excellent SFTP client with a graphical interface for Windows.
4. Remote Desktop Protocols (VNC): Graphical Access
If you need a graphical interface to remotely access your Raspberry Pi, remote desktop protocols like VNC provide a convenient solution. Ensure that you configure VNC securely, with a strong password and encryption.
- TightVNC: A free VNC client and server.
- RealVNC: A more feature-rich VNC solution.
5. Network Utilities
Certain network utilities can assist in diagnosing network problems or observing network traffic. Install these tools directly on your Raspberry Pi:
- `net-tools` (if not already installed): Provides utilities such as `ifconfig` and `netstat` for network configuration and status checks.
- `tcpdump`: A command-line network packet analyzer, which can be used for capturing and inspecting network traffic. Use this to monitor traffic within the WireGuard tunnel for troubleshooting.
Careful selection of the proper software is an essential step in building a secure and efficient remote IoT setup. Ensure that the tools you choose are compatible with your devices, readily available, and meet your security requirements.
Installing WireGuard on Raspberry Pi
WireGuard is an exceptionally secure and efficient modern VPN protocol. Installing WireGuard on your Raspberry Pi is a fundamental step in securing your remote IoT P2P connections. This installation process involves a series of clear steps:
1. Update the System Packages
Begin by ensuring that the package lists and packages on your Raspberry Pi are up-to-date:
sudo apt updatesudo apt upgrade
2. Install WireGuard
WireGuard is usually readily available in the official repositories. Use the following command to install it:
sudo apt install wireguard
3. Generate Keys
WireGuard uses cryptographic keys for secure communication. Generate a private and public key for your Raspberry Pi:
sudo wg genkey | sudo tee /etc/wireguard/privatekey | wg pubkey > /etc/wireguard/publickey
This command generates a private key and saves it to `/etc/wireguard/privatekey`, while simultaneously deriving the public key and storing it in `/etc/wireguard/publickey`. Be sure to securely store your private key.
4. Configure WireGuard Interface
Create a configuration file for your WireGuard interface. This will define the network settings, keys, and peer configurations. Create the configuration file using a text editor, such as nano:
sudo nano /etc/wireguard/wg0.conf
Add the following configuration (replace the example values with your actual keys, IP addresses, and peer details). Heres a basic configuration template:
[Interface]PrivateKey =Address = 10.6.0.1/24ListenPort = 51820
Replace `
5. Configure Peers (Remote IoT Devices)
Add peer configurations. Peers are your remote IoT devices that will connect to the Raspberry Pi via the VPN:
[Peer]PublicKey =AllowedIPs = 10.6.0.2/32 # Replace with the remote device's IP address
Replace `
6. Enable and Start WireGuard
After creating the configuration file, enable and start the WireGuard interface:
sudo wg-quick up wg0
7. Check the Configuration
To verify that WireGuard is running and configured correctly, use the following command:
sudo wg show
This should display information about your WireGuard interface, including the keys, IP addresses, and connected peers. A successful installation means that you've established a secure VPN tunnel.
Installing WireGuard on your Raspberry Pi is a crucial step toward establishing secure, reliable remote IoT P2P connections. Ensure that you follow the instructions accurately, and securely store the generated keys. Regularly test and monitor your connections to confirm they are functioning correctly.
Configuring Your IoT Devices for P2P Connection
Configuring your IoT devices for P2P connections is critical to ensuring secure and reliable communication with your Raspberry Pi. This process involves ensuring that each remote device can establish a secure connection via the WireGuard VPN tunnel, and that they can communicate directly. The configuration process is multifaceted, involving several key steps:
1. WireGuard Installation
The first step is to install WireGuard on each of your remote IoT devices. Follow the same installation steps you used for your Raspberry Pi, ensuring that the operating system and package management system are up to date.
2. Key Generation
Generate a private and public key pair for each of your remote IoT devices. These keys are used for encrypting and authenticating communication. This step is crucial for the secure operation of the VPN.
sudo wg genkey | sudo tee /etc/wireguard/privatekey | wg pubkey > /etc/wireguard/publickey
Store the private key securely on each device. Ensure that the public key is shared with the Raspberry Pi.
3. Configuration File Creation
Create a WireGuard configuration file on each remote IoT device. Use a text editor (e.g., nano) to create a configuration file, typically located at `/etc/wireguard/wg0.conf`. This file defines the network settings and peer configurations specific to that device.
4. Interface Configuration
Configure the WireGuard interface settings within the configuration file. This includes the private key, assigned IP address, and listen port for the device.
[Interface]PrivateKey =Address = 10.6.0.2/32 # Adjust as needed (e.g., 10.6.0.2, 10.6.0.3, etc.)
Replace `
5. Peer Configuration (Raspberry Pi)
Specify the Raspberry Pi as a peer within the remote device's configuration file. This involves the Raspberry Pi's public key, along with the allowed IPs. This is the critical step, allowing the device to connect to the Raspberry Pi via the VPN tunnel.
[Peer]PublicKey =AllowedIPs = 0.0.0.0/0Endpoint = :51820
Replace `
6. Firewall Configuration
Configure the firewall on each remote IoT device to allow traffic through the WireGuard interface. Also, configure the firewall on the Raspberry Pi to forward traffic to the other devices that are part of the VPN. This is a critical part of ensuring traffic can move securely to the devices.
7. Enabling and Starting WireGuard
Enable and start the WireGuard interface on each remote IoT device after configuring the configuration file:
sudo wg-quick up wg0
8. Testing the Connection
Test the connection to verify that it is working correctly. On each remote device, you can ping the Raspberry Pi's IP address on the VPN (e.g., 10.6.0.1). Also, ping other devices on the VPN to verify that they can communicate with each other. In this case, the Raspberry Pi would be at 10.6.0.1, and another device would be at 10.6.0.3.
9. Monitoring and Troubleshooting
Regularly monitor the connections to troubleshoot any issues that arise. Use tools such as `wg show` to check the status of the WireGuard interface and the peers. You can use `tcpdump` to examine the traffic within the WireGuard tunnel. If you run into problems, go back and review your keys, IP addresses, and configuration settings to see if there are any issues. Double-check the key, then IP addresses, and then the connection ports.
Proper configuration of your IoT devices for a P2P connection is the most critical step towards achieving secure remote connectivity. Ensure each device has its own unique public key, a static internal IP address, and the correct public information for your Raspberry Pi. Verify these settings, and then test the connection to make certain that your devices can communicate through the VPN tunnel.
Best Practices for Securing Your IoT Network
Securing an IoT network is a continuous process that requires ongoing vigilance and adherence to industry best practices. The goal is to create a robust defense against potential threats, protect your data, and maintain the integrity of your devices. The following guidelines represent a collection of critical security practices:
1. Strong Passwords and Authentication
- Robust Passwords: Use strong, unique passwords for all devices and accounts. Passwords should be at least 12 characters long, combining uppercase and lowercase letters, numbers, and symbols.
- Multi-Factor Authentication (MFA): Enable MFA wherever possible to add an extra layer of security.
- Regular Password Changes: Regularly rotate your passwords to reduce the risk of compromise.
2. Network Segmentation
- Isolate IoT Devices: Separate your IoT devices from your main network. This limits the potential for attackers to move laterally within your network.
- Virtual LANs (VLANs): Utilize VLANs to segment your network. This will keep traffic separated.
3. Encryption and Secure Protocols
- End-to-End Encryption: Encrypt all data transmitted between your IoT devices and your Raspberry Pi. WireGuard provides this function.
- Use HTTPS: Ensure that all web interfaces and APIs are secured with HTTPS.
- Secure Protocols: Utilize secure protocols such as SFTP and SSH.
4. Regular Updates and Patch Management
- Automated Updates: Configure automatic updates for all your operating systems and software.
- Patch Management: Immediately apply security patches to address vulnerabilities.
- Regular Scanning: Periodically scan your devices for security vulnerabilities.
5. Firewall Configuration
- Restrict Access: Configure your firewall to restrict unnecessary network access.
- Default Deny: Implement a default-deny firewall rule, which blocks all traffic unless explicitly allowed.
- Monitor Firewall Logs: Regularly monitor your firewall logs to detect suspicious activity.
6. Monitoring and Logging
- Comprehensive Logging: Implement detailed logging to record system and application events.
- Security Information and Event Management (SIEM): Integrate SIEM solutions to collect, analyze, and alert on security events.
- Real-Time Monitoring: Monitor your network and devices in real-time for unusual behavior.
7. Physical Security
- Secure Hardware: Physically secure your Raspberry Pi and other IoT devices.
- Restricted Access: Limit physical access to your devices.
8. Network Monitoring Tools
- Intrusion Detection Systems (IDS): Deploy an IDS to detect malicious activity.
- Network Traffic Analysis: Analyze network traffic patterns for anomalies.
9. Incident Response Plan
- Plan Preparation: Develop an incident response plan to handle security breaches.
- Regular Drills: Conduct regular incident response drills to prepare for potential incidents.
By adhering to these best practices, you can significantly improve the security of your IoT network, protect your sensitive data, and enhance the reliability of your devices. The key is to approach security as an ongoing process, continuously monitoring, adapting, and improving your defenses to meet evolving threats.
Where to Download Secure IoT P2P Raspberry Pi Resources
Finding trusted resources is essential for building a secure remote IoT P2P setup using a Raspberry Pi. The following resources offer valuable tools, documentation, and community support:
1. Official Documentation
- Raspberry Pi Foundation: The Raspberry Pi Foundation website (raspberrypi.com) provides comprehensive documentation, tutorials, and guides for setting up and configuring your Raspberry Pi.
- WireGuard: The official WireGuard website (wireguard.com) offers detailed documentation on the protocol, installation instructions, and configuration guides.
2. Software Repositories
- Raspberry Pi OS Repositories: These repositories are the primary source for installing software on your Raspberry Pi. Use `apt update` and `apt install` to access software.
- Open-Source Projects: Websites such as GitHub (github.com) host numerous open-source projects and tools relevant to IoT and security, including WireGuard configurations and example scripts.
3. Community Forums and Support
- Raspberry Pi Forums: The Raspberry Pi forums (raspberrypi.org/forums) are a valuable resource for getting help, sharing experiences, and learning from other users.
- WireGuard Mailing Lists and Forums: Join the WireGuard community forums to seek assistance and learn from other users and experts.
- Stack Overflow: Use Stack Overflow (stackoverflow.com) to find answers to technical questions and troubleshoot issues.
4. Security Resources
- NIST: The National Institute of Standards and Technology (NIST) website (nist.gov) offers valuable security guidelines, standards, and best practices for IoT.
- SANS Institute: The SANS Institute (sans.org) provides security training, certifications, and resources.
5. Free Downloadable Resources
- Scripts and Configuration Files: Many tutorials and guides provide downloadable scripts and example configuration files to simplify setup. Look for reputable sources.
- Security Tools: Access free and open-source security tools such as SSH clients and SFTP clients to ensure secure connections.
To safeguard your project, download resources from trusted sources, verify file integrity, and maintain caution when downloading and executing scripts or software from unknown sources. The combination of official documentation, community support, and credible security resources will equip you with the knowledge and tools needed to build a secure remote IoT P2P connection.
The ability to securely connect remote IoT devices is more critical than ever. This guide provides a detailed roadmap, covering everything from initial setup to advanced security practices. By following the steps outlined, you will be able to create a robust and secure P2P connection that protects your data and enhances the functionality of your devices.


Detail Author:
- Name : Brycen Ritchie
- Username : abechtelar
- Email : nicholaus.lind@hotmail.com
- Birthdate : 1977-09-30
- Address : 932 Nolan Street Apt. 440 Myrtisstad, ID 52983-8120
- Phone : +1.662.916.4319
- Company : Lebsack-Beier
- Job : Gas Pumping Station Operator
- Bio : Et voluptate similique animi consectetur voluptas. Quidem deleniti magnam in aspernatur architecto. Facere ullam dolores fuga nulla. Ut et iusto officiis vero ea autem possimus.
Socials
instagram:
- url : https://instagram.com/torphye
- username : torphye
- bio : Quam aut ullam eum aut. Tenetur sit sit et consequatur. Voluptas voluptatem asperiores dicta odit.
- followers : 926
- following : 2850
linkedin:
- url : https://linkedin.com/in/ephraim_xx
- username : ephraim_xx
- bio : At nobis omnis sed expedita.
- followers : 6175
- following : 880
tiktok:
- url : https://tiktok.com/@ephraim_id
- username : ephraim_id
- bio : Deleniti ut animi at explicabo fuga eveniet. Fugit iure quia quam a magnam et.
- followers : 4009
- following : 2646
twitter:
- url : https://twitter.com/torphye
- username : torphye
- bio : Quod molestias consequatur aut voluptatem repellendus. Ratione quis aut et deserunt aliquid. Eligendi aliquid voluptatem tempora suscipit minima.
- followers : 6259
- following : 2453