In an era defined by ubiquitous connectivity, have you ever considered the inherent vulnerabilities of your Internet of Things (IoT) devices? Securing remote IoT devices using Peer-to-Peer (P2P) SSH on Windows 10 isn't just a technical consideration; it's a crucial necessity for anyone navigating the digital landscape, from tech enthusiasts to seasoned professionals.
The integration of IoT devices into our daily lives, from smart home appliances to industrial sensors, has dramatically expanded the attack surface for cyber threats. Consequently, safeguarding these devices against unauthorized access and data breaches is paramount. This is where the power of Secure Shell (SSH) and P2P connections, particularly on the widely-used Windows 10 platform, comes into play. SSH provides a secure means of communication by encrypting data transmitted between devices, while P2P connections establish direct links, bypassing the complexities of traditional network configurations.
To fully grasp the significance of this technology, let's consider a typical scenario. Imagine a smart agriculture setup, where sensors are deployed across a remote field, monitoring soil conditions, temperature, and humidity. These sensors, as IoT devices, must transmit data back to a central control system for analysis and decision-making. Without secure communication, this data could be intercepted, manipulated, or used to disrupt operations. Implementing P2P SSH, however, creates a secure, encrypted tunnel, ensuring that only authorized parties can access and interpret the information.
- Exploring Gore Sites Legality Ethics Risks
- Alternatives To Movierulz For Kannada Movies Watch Legally
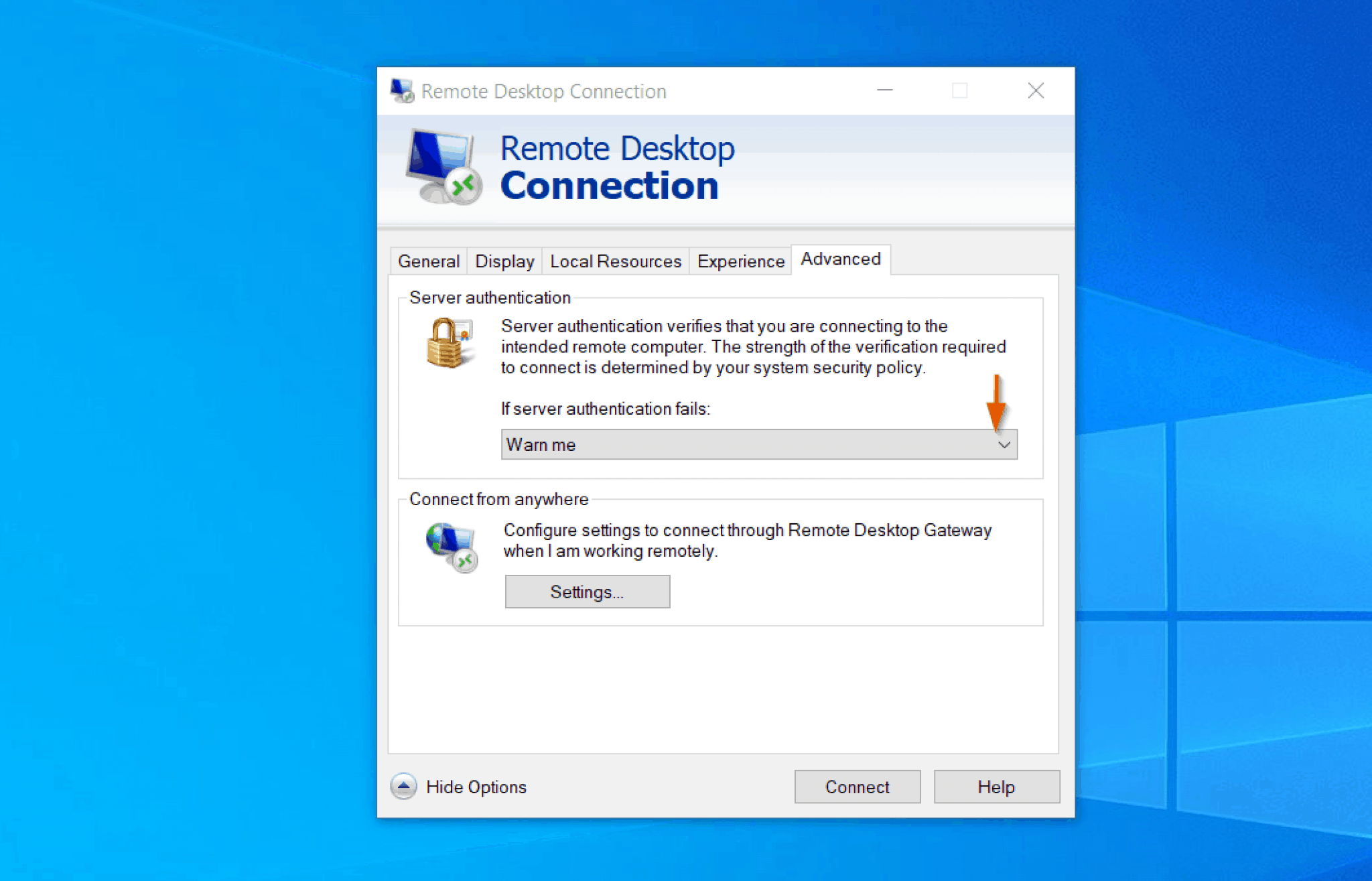
One of the greatest strengths of Windows 10 lies in its native OpenSSH capabilities. This built-in functionality provides the essential tools for establishing secure, direct connections, making the implementation process more streamlined and accessible than ever before. This eliminates the need for third-party software or complex setups, streamlining the process. Leveraging P2P SSH also provides the flexibility to manage devices without the need for static IP addresses or port forwarding, often a challenge in dynamic network environments.
This guide seeks to demystify the process of securely connecting remote IoT devices utilizing P2P SSH on Windows 10. We'll start with the fundamentals of SSH, explore the benefits of P2P connections, and provide a step-by-step guide to implementing these technologies. By the end, you'll have a clear understanding of how to establish secure communication channels, protect your data from malicious actors, and enhance the overall security of your IoT ecosystem.
Before proceeding, let's delve into some background information about SSH, and how it protects your data, SSH, or Secure Shell, is a cryptographic network protocol that provides secure access to a remote server or device. SSH works by encrypting all data transmitted between the client and the server, ensuring that even if data is intercepted, it cannot be easily read or understood. The fundamental principle of SSH hinges on the establishment of a secure, encrypted channel for communication. This channel ensures that all data transmitted between your local machine and the remote IoT device is protected from eavesdropping and tampering. This is achieved through the use of cryptographic techniques, which scramble the data into an unreadable format. Only the intended recipient, possessing the appropriate decryption keys, can then translate the scrambled data back into its original, readable form.
- Kyle Richards Nicky Hilton Wedding Drama Uninvited Reinvited
- Greys Anatomy Denny Duquettes Death Izzies Fate
P2P connections, the "Peer-to-Peer" approach, further enhance security and efficiency. Traditional client-server models require a central server to mediate communication between devices, creating a single point of failure and introducing potential latency. P2P, however, enables direct communication between the devices, removing the central server and reducing reliance on complex network configurations. This streamlined approach enhances security by reducing the attack surface, while also optimizing performance.
Let's summarize the key advantages of using P2P SSH for your IoT devices:
- Enhanced Security: Encryption protects your data from eavesdropping and tampering.
- Direct Connections: Bypassing the need for a central server reduces the attack surface.
- Simplified Configuration: Eliminates complex network settings such as port forwarding.
- Increased Reliability: Direct connections enhance the stability of communication.
A practical implementation of P2P SSH on Windows 10 often includes using software like PuTTY. PuTTY is a free and open-source terminal emulator application that can act as a client for various network protocols, including SSH. While Windows 10's native OpenSSH capabilities provide the core features, PuTTY is often preferred for its user-friendly interface and additional features. The combination of OpenSSH and a client like PuTTY allows you to establish secure and direct connections with your IoT devices.
The first step is always the foundation: ensuring your systems are up-to-date. Regularly patching your Windows 10 operating system and any associated software, including the OpenSSH client, is paramount. Updates frequently include security patches that address known vulnerabilities. Secondly, strong authentication is vital. Opt for robust passwords, and consider the use of multi-factor authentication (MFA) if your devices and network support it. MFA adds an extra layer of security by requiring a second form of verification, such as a code from an app, in addition to the password.
You might want to consider an even more advanced approach, by creating a VPN, which will help you create a secure tunnel for your data as well. VPNs encrypt all traffic passing through them, making it extremely difficult for cybercriminals to intercept or access sensitive information, and protect you from the dangers of unprotected public Wi-Fi networks, providing peace of mind that your data is secure, no matter where you are. The benefits include not only security but also it can hide your IP address and location, and access content that is geo-restricted.
Remember, the key takeaway is that securing your IoT devices using P2P SSH on Windows 10 is not just about implementing technology; it's about creating a robust defense against the evolving threats in the digital age. By understanding the fundamentals of SSH, leveraging the benefits of P2P connections, and implementing these techniques correctly, you can ensure that your IoT ecosystem remains secure, reliable, and protected from malicious actors.
The goal is to create a secure and efficient communication channel for your devices. To do this, start by setting up an SSH client on your Windows 10 machine. Configure port forwarding if necessary (although P2P SSH often negates this), and ensure your IoT device is accessible. Consider a range of security enhancements, like robust passwords and regularly updating software, to protect against potential threats.


Detail Author:
- Name : Dr. Theodore Marks II
- Username : lebsack.magali
- Email : virgie.huel@yahoo.com
- Birthdate : 1988-05-21
- Address : 883 Rutherford Motorway North Grahamside, SC 65236-1371
- Phone : 929-270-7930
- Company : Christiansen LLC
- Job : Dancer
- Bio : Esse non unde deserunt porro. Rerum quia in iusto reprehenderit. Reprehenderit a ab laudantium. Ipsum maxime tempore et quisquam illo ratione vero.
Socials
instagram:
- url : https://instagram.com/korey3821
- username : korey3821
- bio : Vero quo cum tenetur sit nisi natus. Qui est aut quisquam tempora qui consequatur expedita.
- followers : 2637
- following : 524
twitter:
- url : https://twitter.com/korey.cormier
- username : korey.cormier
- bio : Nobis nam tempore alias. Adipisci non minima et tempora. Maxime et et minus omnis quibusdam.
- followers : 768
- following : 2868