Can you truly secure your Internet of Things (IoT) devices from prying eyes? The ability to establish secure, direct connections to your IoT devices is not just a technological convenience, but a fundamental necessity in today's interconnected world.
Whether you're a seasoned professional managing industrial IoT systems or a passionate hobbyist tinkering with home automation, the imperative to connect securely is undeniable. This article serves as your comprehensive guide, meticulously outlining the steps needed to establish a secure connection using p2p SSH on your Windows 10 machine. We'll navigate the process, ensuring that your IoT devices remain shielded from unauthorized access and that your data is protected. We'll delve into the fundamentals of SSH, the advantages of p2p connections, and furnish you with practical, actionable steps to implement these technologies. By the end of this guide, you'll possess a clear understanding of how to securely connect remote IoT devices using p2p SSH on Windows 10, along with advanced techniques and tips to fortify your network's security.
To begin with, let's examine the basic components and processes involved in establishing a secure p2p SSH connection to your IoT devices on Windows 10. Here is a summary of these processes.
- Ganges River Facts Countries Significance Learn Now
- Ganges River Countries Significance Facts Your Guide
| Component | Description | Action |
|---|---|---|
| SSH Client | The software used to initiate and manage SSH connections. | Install and configure an SSH client on your Windows 10 machine (e.g., PuTTY or Windows 10's native OpenSSH). |
| IoT Device | The device you wish to connect to remotely (e.g., a Raspberry Pi, Arduino, or any other IoT device). | Ensure your IoT device has SSH enabled and is accessible on your local network. It should also have a static or reserved IP address. |
| Router | The device that connects your local network to the internet. | Configure port forwarding on your router to direct SSH traffic to your Windows 10 machine or the IoT device itself, as needed. |
| Network Configuration | The settings required for establishing a secure connection. | Set up your network for remote access and verify the security measures are in place. |
| Security Measures | The practices that ensure that your data is encrypted and your connection stays private. | Implement security measures and follow best practices to maintain a secure and reliable setup, and always update credentials and software to prevent vulnerabilities. |
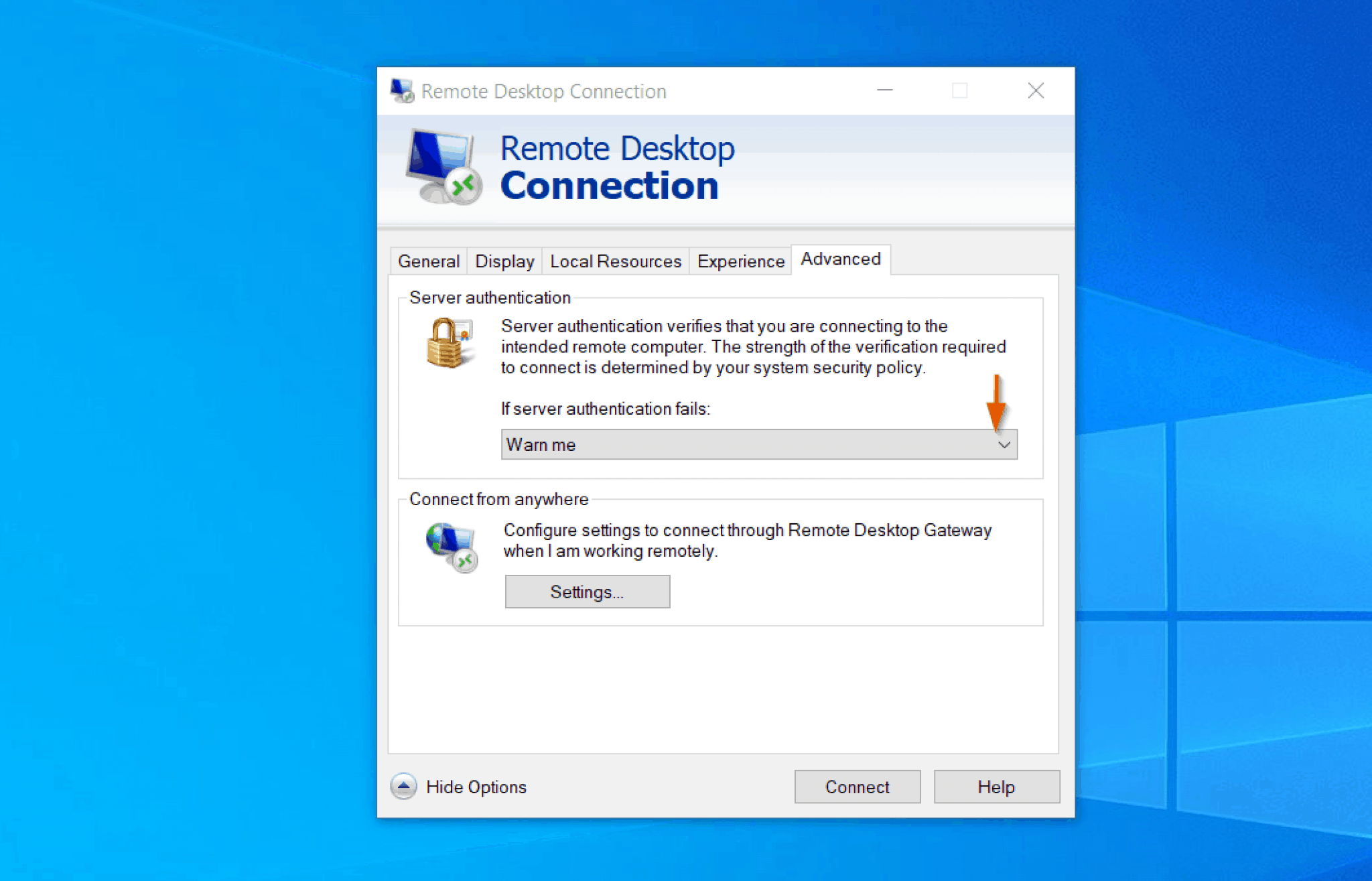
The first crucial step is setting up an SSH client on your Windows 10 machine. Windows 10's native OpenSSH client offers all the necessary features to establish secure, direct connections, eliminating the need for third-party software. The alternative is to use a third-party client, the popular option being PuTTY.
Configuring your IoT device is the second major step. This may vary based on the type of device and its operating system. Typically, you'll need to enable SSH on the device and ensure it has a static IP address or a reserved IP address on your local network. This ensures that the device's IP address doesn't change, which is critical for maintaining a reliable connection. The device will also need a user account with appropriate SSH permissions.
Next, you'll need to configure port forwarding on your router. This is essential for allowing external access to your device. You will direct incoming SSH traffic (typically on port 22) to your Windows 10 machine. The specific instructions for doing this will vary depending on your router model. However, the general process involves accessing your router's configuration page (usually through a web browser using its IP address), navigating to the port forwarding section, and creating a rule that forwards traffic on port 22 to the internal IP address of your Windows 10 machine or the IoT device and ensure that the correct protocol (TCP) is selected.
- Steak Doneness Guide Find Your Perfect Temperature
- Stray Kids Members Ages Profiles From Oldest To Youngest
Once you have set up an SSH client on your Windows 10 machine, configured your IoT device for SSH access, and configured port forwarding on your router, you are ready to establish a secure connection. You can use the SSH client to connect to your IoT device from anywhere. The command will look something like this: `ssh [username]@[your_public_ip_address] -p [port_forwarded_to_windows_or_device]`. The username is the username you have set up on your IoT device.
By enabling SSH on Windows 10, configuring your IoT device, and setting up your network for remote access, you can efficiently manage your connected devices from anywhere. Remember that implementing security measures and following best practices will help you maintain a secure and reliable setup. Regularly update your security settings and be vigilant about security alerts.
This method ensures that your data remains encrypted, and your connection stays private, even when accessing devices over the internet. By using p2p SSH, you can establish encrypted communication channels that safeguard your data from malicious actors. Connecting to remote IoT devices securely doesn't have to be complicated or expensive. By leveraging p2p SSH with PuTTY, you can establish secure and direct connections, enhancing the management and monitoring of your IoT infrastructure.
The advantages of p2p SSH are numerous. It offers a secure and encrypted connection. It provides direct access to your IoT device. It enhances management and monitoring of your IoT infrastructure. Moreover, with p2p SSH, you don't need to rely on third-party services or cloud-based platforms, offering greater control over your data and connections.
In today's interconnected world, securely connecting to remote IoT devices using p2p SSH on Windows 10 has become a critical need for individuals and businesses alike. The ability to remotely access, manage, and monitor your devices from anywhere can significantly enhance productivity, efficiency, and convenience. Whether you're a professional managing a network of industrial IoT devices or a hobbyist working on your home automation system, the skills and knowledge of securely connecting remote IoT devices using p2p SSH on Windows 10 is invaluable.
This process involves installing an SSH client, configuring it, and establishing an SSH connection. Once installed, it's essential to configure the SSH client with the correct information, including the IP address, port number, and credentials for your IoT device. This typically involves entering the device's IP address, port number (usually 22), and your username and password. You might also need to configure the SSH client with any necessary proxy settings.
As a precaution, always use strong, unique passwords for your IoT devices. Regularly change these passwords and consider implementing multi-factor authentication. Furthermore, keep your SSH client and the operating system of your IoT devices up to date with the latest security patches. This minimizes the risk of vulnerabilities that could be exploited by malicious actors. Finally, consider using key-based authentication instead of passwords for an even more secure connection. This involves generating a key pair (a private and a public key) and installing the public key on your IoT device. Then, when you connect, you will be authenticated using the private key on your Windows 10 machine, eliminating the need to enter a password.
To reiterate, to successfully set up a secure connection, youll need to set up an SSH client on your Windows 10 machine, configure port forwarding on your router, and ensure your IoT device is accessible. Windows 10's native OpenSSH capabilities provide all the necessary features to establish secure, direct connections. Remember, whether you're monitoring home automation systems or managing industrial IoT devices, the ability to connect securely is vital.
In this context, consider these best practices for ensuring secure and reliable connections. First, always use strong, unique passwords for your SSH user accounts on your IoT devices. These passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols. Regularly change your passwords, ideally every 90 days. Second, ensure your router's firmware is up-to-date. Router firmware updates often include crucial security patches that address known vulnerabilities. Third, consider using a firewall on your Windows 10 machine to further restrict access to your SSH port. This adds an extra layer of protection, preventing unauthorized access even if your SSH credentials are compromised.
Further, disable password-based authentication if possible and opt for key-based authentication. Key-based authentication is more secure as it relies on cryptographic keys rather than passwords. Also, configure your SSH server to only allow connections from specific IP addresses. This can drastically reduce the attack surface of your SSH server. Lastly, regularly audit your SSH configuration and logs. Check the logs for any suspicious activity or failed login attempts. This will help you identify and address potential security breaches proactively.
In conclusion, securely connecting remote IoT devices using p2p SSH on Windows 10 is an essential skill in today's digital landscape. By understanding the fundamentals of SSH, the benefits of p2p connections, and following the practical steps outlined in this article, you can establish a secure and reliable setup. Remember to prioritize security measures and best practices to safeguard your data and maintain the integrity of your IoT devices. From the initial setup of your SSH client to the configuration of your router and the IoT devices themselves, each step plays a crucial role in creating a secure environment. With a commitment to best practices and a proactive approach to security, you can confidently manage and monitor your connected devices from anywhere in the world.


Detail Author:
- Name : Dr. Emmy Raynor I
- Username : thiel.emmett
- Email : frami.imani@adams.info
- Birthdate : 1984-12-23
- Address : 513 Gabriella Shores Suite 546 East Edenhaven, VA 07432-2631
- Phone : +12837332560
- Company : Nitzsche-Heidenreich
- Job : Typesetter
- Bio : Aliquam distinctio doloribus ipsa animi explicabo. Sapiente dolor unde et odio et incidunt. Sit quia et eum iure. Impedit cum sed recusandae qui quo optio placeat veritatis.
Socials
linkedin:
- url : https://linkedin.com/in/terence.jenkins
- username : terence.jenkins
- bio : Nihil tenetur dolorem quasi quam optio ullam cum.
- followers : 5655
- following : 184
twitter:
- url : https://twitter.com/terence_xx
- username : terence_xx
- bio : Et ratione ut voluptas officiis dolorum. Eveniet et vel fugiat dolorem. Perferendis dolor culpa soluta dolor ipsam. Maiores necessitatibus sit vel quo.
- followers : 4290
- following : 2553
facebook:
- url : https://facebook.com/terence_official
- username : terence_official
- bio : Nobis reprehenderit dignissimos et debitis.
- followers : 3457
- following : 2219
tiktok:
- url : https://tiktok.com/@terence.jenkins
- username : terence.jenkins
- bio : Ab dicta modi eum eos occaecati cumque.
- followers : 4117
- following : 1212